Discover and Protect API Endpoints
As organizations advance in their cloud journey leveraging more cloud native technologies, HTTP-based APIs continue to proliferate as entry points to applications and to microservices. Breaches observed in recent years demonstrate the high risk associated with this rapidly expanding attack surface of APIs, raising concerns about exposing highly sensitive data and meeting the challenges with detection and effective monitoring of APIs.
This ever-growing attack surface is tricky to discover as it is dynamic, maintained by multiple teams, may be hosted in multiple services or workloads, and it’s often the case that customers need help in discovering and keeping track of it. Security teams require a simple, yet effective way, to discover APIs exposed in their deployment and evaluate the risks associated with them. Prisma Cloud makes the security teams' lives much easier by managing the security of their APIs along with all other cloud assets using a single pane of glass.
Prisma Cloud combines agent-based, agentless techniques, and data gathered on cloud accounts. This comprehensive approach automatically scans traffic and configurations within the deployment, enabling effective discovery of API endpoints.
1. Increase API visibility in your deployment
API Discovery and Profiling is the starting point of every customer’s API security journey. In order to continuously and automatically discover API endpoints, a broad set of inline and Out-of-Band integrations into public cloud and on-premise environments are made available for Prisma Cloud customers either by deploying Prisma Cloud Defenders or with VPC traffic mirroring (available for AWS).
In order to start inspecting HTTP traffic and discover APIs
- Create a WAAS rule.
- Agent based - Create WAAS rule for containers, hosts or app embedded.
- Agentless (available for AWS) - No Defenders required, add WAAS agentless rules to discover new API with AWS VPC traffic mirroring.
- Verify that API Discovery is enabled.
- Make sure that you have selected Runtime Security on the Prisma Cloud switcher.
- Select an existing rule on Defend > WAAS to verify that API endpoint discovery is enabled.
In addition to discovery of API endpoints, WAAS monitors traffic for a wide variety of malicious activity:
- Web attacks
- Bot activity
- Denial of Service (DoS)
- Unauthorized access
- API abuse
- Sensitive data exposure
- Exploitation of known vulnerabilities and customer specific threats
2. Assess the level of risk in discovered APIs
Security involves the process of managing risks and allocating resources strategically to lower the overall risk, beginning with the most vulnerable assets. Following the discovery phase, the next step is conducting a risk assessment to determine which APIs should take precedence for prioritization.
Once WAAS rules are enabled, discovered API endpoints will start showing up in Prisma Cloud API endpoint inventory

APIs can be grouped by domain name, services, accounts etc.

The Risk factors columns indicate critical path risks identified in the endpoints:
- Endpoints accessible from the internet.
- Endpoints that do not require authentication to be accessed.
- Endpoints with sensitive data such as Credit card, PII, ID query parameter, Session cookies, and so on. The sensitive data is defined under Defend > WAAS > Sensitive data.
- Endpoints where incidents have been observed.
Select an endpoint to view the side panel with additional details and statistics, such as request and response size ranges, sensitive data detected, message structure.
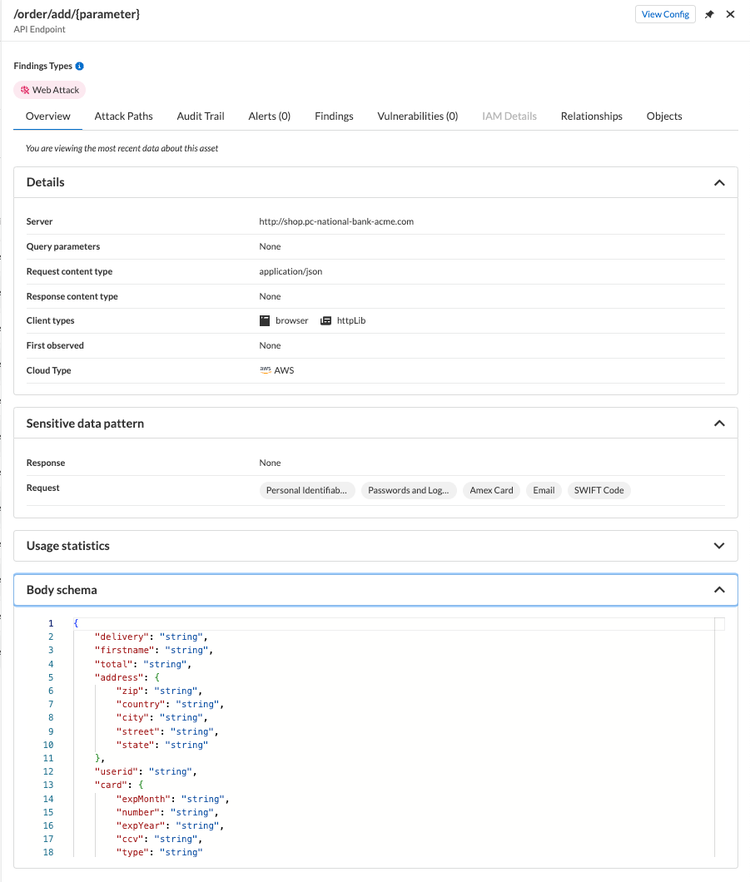
Based on the risk profile we should prioritize preventive measures such as in-line protections for the riskier parts of our API deployments and perhaps deploy monitoring measures for all others.
3. Investigate incidents and suspicious activity
Investigating incidents and suspicious activity is invaluable in protecting web assets and maintaining their integrity. It serves as an early warning process, allowing organizations to detect and respond to potential threats before they escalate into major breaches. By thoroughly examining WAAS events, users can uncover vulnerabilities, identify malicious actors, and fine-tune security measures. Furthermore, incident investigations provide opportunities for learning and continuous improvement, strengthening overall cybersecurity posture. In a rapidly evolving threat landscape, proactive investigation is a key activity of effective cybersecurity.
WAAS analytics allows for the review of incidents by analyzing events across various dimensions, inspecting individual requests, and applying filtering to focus on common characteristics or trends.
To access the analytics, select Runtime Security on the Prisma Cloud switcher and select Monitor > Events and select the relevant page for your workloads. For example, `WAAS for containers`, `WAAS for hosts`.
